reflected DOM vulnerability
- Maryam Ziaee
- Sep 16
- 2 min read
Reflected DOM vulnerabilities occur when the server-side application processes data from a request and echoes the data in the response.

Tools: Burp Suite, OWASP ZAP, Linux


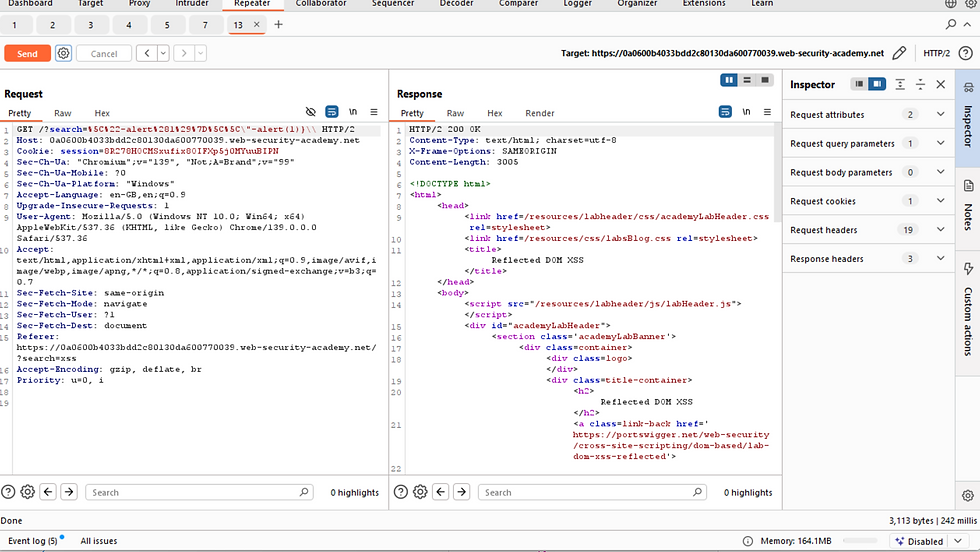
Description of the vulnerability type (DOM XSS
Security impact-Recommendations
Alert in OWASP


Content security policy header not set
. The recommendation is to implement a strict CSP to reduce the risk and impact of client-side attacks like XSS, data exfiltration, and clickjacking.
Cookie with SameSite attribute none
It means the browser will send it in all cross-site requests, which can increase the risk of Cross-Site Request Forgery (CSRF) and other cross-origin attacks unless it’s properly secured.
Recommendation for SameSite=None Cookies
The Strict-Transport-Security (HSTS) header is not set,
Browsers won’t automatically enforce HTTPS for your site — leaving it vulnerable to SSL stripping and man-in-the-middle downgrade attacks.
Recommendation for Missing HSTS Header
Enable HTTP Strict Transport Security (HSTS)
Timestamp disclosure -Unix
Recommendation for Unix Timestamp Disclosure
Avoid exposing raw timestamps where not needed
Remove unnecessary debug or verbose output.
X-Content-Type-Options Header Missing
Recommendation for Missing X-Content-Type-Options Header
Set the header to disable MIME type sniffing
Re-examine Cache-Control Directives
When Cache-Control directives are weak, missing, or overly permissive. Sensitive pages (like account, banking, or session-based content) might be stored in the browser cache or intermediate caches — allowing local attackers (e.g., shared computer users) or proxy attackers to retrieve them.
Recommendation for Cache-Control Directives
For sensitive, authenticated, or dynamic pages
Disable caching completely in browsers and proxies
Retrieved from Cache
When sensitive pages or data can be retrieved from the browser or intermediary cache, it means an attacker (or another user on a shared system) could potentially view private information after the original user has logged out.
Recommendation for “Retrieved from Cache” Issues
Prevent caching of sensitive content
Use HTTP headers to ensure pages containing personal or authenticated data are never stored in browser or proxy caches
Session Management Respond Identified
If the session management response reveals sensitive session information or shows insecure practices, it can lead to session hijacking, fixation, or other authentication bypass attacks.
Recommendation for Session Management Findings
Use Secure Cookie Attributes



Comments